🔑 sup3rS3cretMes5age!
sup3rS3cretMes5age! is a tool for making self destructing messages work, and you don't need Snapchat's engineering team to run it. You also don't need to know 1337speak, either but it doesn't hurt.
Built by Eran Chetzroni, the rationale behind sup3rS3cretMes5age! is laid out in an awesome blog post:

I'll lay out the premise quickly here for the impatient:
- Use Hashicorp Vault to keep your secrets safe (it's good at that)
- There are lots of other encrypted pastebins, but they're not necessarily easy to self host, and don't use Vault
- It's really easy to use for users, and deletes messages after they're read
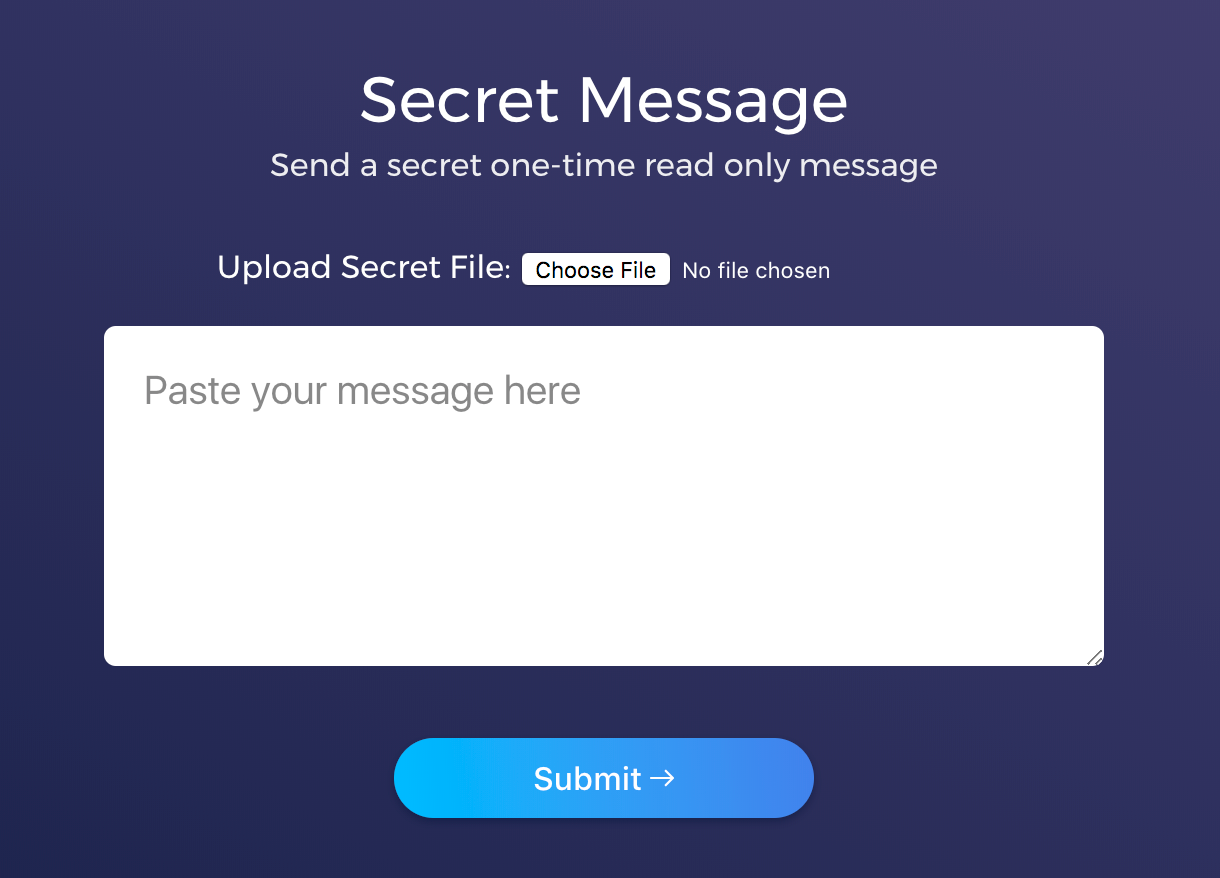
If you need some nice self-hosted secret sharing software, look no further! Here's what it looks like:
🌠 Features
sup3rS3cretMes5age! has a bunch of features, let's run through them real quick
- Securely share notes & secrets
Dockerfileis available,docker-compose.yamlalso in the repo- Enterprise-grade secret storage with HashiCorp Vault
- In use at an actual tech organization
- Golang codebase (easy to read & build)
Unfortunately sup3rS3cretMes5age! does not have an official docker image, but at least it's not terribly too hard to build.
🤖 As described by AI
The GitHub project "sup3rS3cretMes5age" is a simple to use and deploy, one-time self-destruct messaging service that uses HashiCorp Vault as its backend. It's designed for secure communication, ensuring that messages are automatically deleted after being read. The project is written in Go and is licensed under the MIT license.
📺 Watch this
There isn't much content on sup3rS3cretMes5age! itself since it's just a small project, but here's a classic intro to Hashicorp Vault, which is used to store secrets:
👟 Getting started
sup3rS3cretMes5age! is built in Golang and easy to build locally, but unfortunately it doesn't have an official docker build (only available Dockerfile and docker-compose.yaml) so there's a bit of work if you want to get it running locally.
🐀 Golang manual build
If you want to build and run the program from scratch you can do so with Golang pretty easily.
Before you do anything you'll want to install the Golang toolchain (and maybe learn a bit about Golang!).
After you've got go set up on your computer, clone the repo:
git clone git@github.com:algolia/sup3rS3cretMes5age.gitThen from inside the created sup3rS3cretMes5age folder we can do the usual go build
go buildAfter a short wait, you'll have the sup3rS3cretMes5age binary in your folder:
tree sup3rS3cretMes5age
sup3rS3cretMes5age
├── CODEOWNERS
├── Dockerfile
├── LICENSE
├── Makefile
├── README.md
├── charts
│ ├── ...
│ └── supersecretmessage
│ ├── ...
│ └── values.yaml
├── config.go
├── docker-compose.yml
├── go.mod
├── go.sum
├── handlers.go
├── handlers_test.go
├── main.go
├── static
│ ├── ...
│ └── robots.txt
├── sup3rS3cretMes5age <---- here it is!
├── vault.go
└── vault_test.go
7 directories, 44 files(Wondering how I generated the listing above? Check out tree or the newer written-in-Rust erdtree)
Much of the configuration is done via ENV variables, so you can export some then start the binary (just like the README):
export VAULT_ADDR=http://vault:8200
export VAULT_TOKEN=root
export SUPERSECRETMESSAGE_HTTP_BINDING_ADDRESS=:80
sup3rS3cretMes5age🐳 Docker build
If you want to use docker, you'll have to build your own image using the Dockerfile in the repo.
As of posting time, it looks like this:
FROM golang:1.18 AS builder
WORKDIR /go/src/github.com/algolia/sup3rS3cretMes5age
ADD . .
RUN go mod download
RUN CGO_ENABLED=0 GOOS=linux go build -o sup3rS3cretMes5age .
FROM alpine:latest
ENV \
VAULT_ADDR \
VAULT_TOKEN \
SUPERSECRETMESSAGE_HTTP_BINDING_ADDRESS \
SUPERSECRETMESSAGE_HTTPS_BINDING_ADDRESS \
SUPERSECRETMESSAGE_HTTPS_REDIRECT_ENABLED \
SUPERSECRETMESSAGE_TLS_AUTO_DOMAIN \
SUPERSECRETMESSAGE_TLS_CERT_FILEPATH \
SUPERSECRETMESSAGE_TLS_CERT_KEY_FILEPATH \
SUPERSECRETMESSAGE_VAULT_PREFIX
RUN \
apk add --no-cache ca-certificates ;\
mkdir -p /opt/supersecret/static
WORKDIR /opt/supersecret
COPY --from=builder /go/src/github.com/algolia/sup3rS3cretMes5age/sup3rS3cretMes5age .
COPY static /opt/supersecret/static
CMD [ "./sup3rS3cretMes5age" ]As you can see it's pretty similar to the Golang manual build, and a nice easy to understand
🧑💻 Want to get involved?
The project is pretty stable at this point but check out the issue tracker and see if there's anywhere you can contribute!


